Introduction
Ensuring audit and compliance on Ubuntu server environments is a critical step for organizations aiming to secure sensitive data, meet regulatory standards, and respond effectively to security incidents. Compliance standards like PCI-DSS, GDPR, HIPAA, and ISO/IEC 27001 mandate robust auditing, logging, and reporting mechanisms to ensure accountability and data protection.
This article provides a comprehensive guide to configuring audit rules, generating reports, identifying suspicious activity, and implementing best practices to maintain compliance on Ubuntu 22.04 servers.
Previous articles:
01. Introduction to Ubuntu Server – SysOSX: AI & Cloud
02. How to Setup Your First Ubuntu Server: A Beginner’s Guide – SysOSX: AI & Cloud
03.Mastering the Linux Command Line for Ubuntu Server – SysOSX: AI & Cloud
04. Managing Users and Permissions on Ubuntu Server: A Comprehensive Guide – SysOSX: AI & Cloud
05. Networking Basics for Ubuntu Server: A Comprehensive Guide – SysOSX: AI & Cloud
06. Installing and Managing Software on Ubuntu Server: A Complete Guide – SysOSX: AI & Cloud
07.Patching and Updating Ubuntu Server: A Comprehensive Guide – SysOSX: AI & Cloud
08. Securing Your Ubuntu Server: Practical Steps for Hardening and Protection – SysOSX: AI & Cloud
09. Ubuntu server auditing and logging
10. System Monitoring Tools for Ubuntu Server: A Comprehensive Guide – SysOSX: AI & Cloud
11. Centralized Logging for ubuntu server: a must read guide – SysOSX: AI & Cloud
Table of Contents
- Why Compliance Audits Matter
- Compliance Standard Requirements Cheat Sheet
- Advanced rule for compliance auditing
- Advanced Compliance Tools
- FAQ: Common Compliance Challenges
- Compliance Maintenance Checklist
Why Compliance Audits Matter
78% of organizations failed initial PCI-DSS audits due to inadequate logging (2023 Verizon Report)
Real-World Breach Example:
A healthcare provider faced $1.2M HIPAA fines after failing to audit access to patient records stored on Ubuntu servers. Proper auditctl rules could have detected the unauthorized access.
Compliance Standard Requirements Cheat Sheet
| Standard | Key Ubuntu Audit Requirements | Relevant Tools |
|---|---|---|
| PCI-DSS | File integrity monitoring, user activity logs | auditd + AIDE |
| GDPR | Data access tracking, 72-hour breach reporting | aureport + ELK |
| HIPAA | ePHI access monitoring, 6-year log retention | auditctl + Splunk |
| ISO 27001 | Risk assessment proof, access control logs | Lynis + OpenSCAP |
Using auditctl to Configure Audit Rules (basics)
The Linux Audit Framework, available on Ubuntu 22.04, is a powerful tool for monitoring system activities. The auditctl command is used to create and manage audit rules that track specific events on your server.
Step 1: Install the Audit Framework
Before configuring audit rules, ensure the audit framework is installed:
sudo apt update
sudo apt install auditd
Step 2: Define Audit Rules
Audit rules specify what activities to monitor. Here are common examples:
- Monitor File Access:
Track modifications to critical files, such as/etc/passwd:
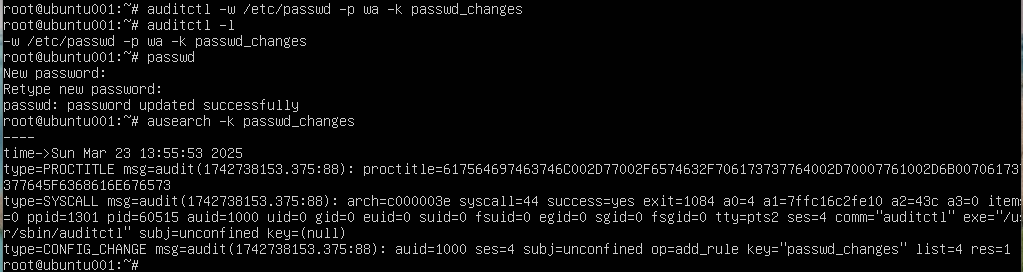
sudo auditctl -w /etc/passwd -p wa -k passwd_changes
This rule monitors write (w) and attribute changes (a) to the /etc/passwd file.
- Monitor Login and Logout Events:
Track user login/logout activity:
sudo auditctl -a always,exit -F arch=b64 -S execve -F key=login_activity
- Monitor Unauthorized Access:
Detect access attempts to sensitive directories:
sudo auditctl -w /var/www/html -p rwxa -k web_access
Step 3: Persist Audit Rules
Audit rules are temporary unless persisted. Add rules to /etc/audit/audit.rules to make them permanent:
-w /etc/passwd -p wa -k passwd_changes
-a always,exit -F arch=b64 -S execve -F key=login_activity
Restart the audit daemon to apply changes, sudo systemctl restart auditd is not working, you need to kill it and start it again to make new configuration take effect:
sudo systemctl kill auditd
sudo systemctl start auditd
Step 4: Verify Active Audit Rules
List all active audit rules to confirm they are applied:
sudo auditctl -l
Advanced rule for compliance auditing
PCI-DSS Rules (/etc/audit/rules.d/pci-dss.rules):
# Monitor payment processing directory
-w /var/lib/payment_processor -p rwxa -k pci_processing
# Track sudo usage
-a always,exit -F arch=b64 -S execve -C uid!=euid -F key=sudo_esc
GDPR Rules (/etc/audit/rules.d/gdpr.rules):
# Monitor database access
-w /var/lib/mysql -p rw -k gdpr_data
# Log user account changes
-w /etc/shadow -p wa -k user_changes
3. Persist Rules Across Reboots
sudo auditctl -R /etc/audit/rules.d/pci-dss.rules
sudo augenrules --load
Generating Audit Reports and Identifying Suspicious Activity
Once audit rules are configured, the next step is to analyze logs and generate reports to identify suspicious activity or compliance violations.
1. View Audit Logs
Audit logs are stored in /var/log/audit/audit.log. Use the ausearch command to query logs:
sudo ausearch -k passwd_changes
This retrieves all events tagged with the keyword passwd_changes.
2. Generate Reports with aureport
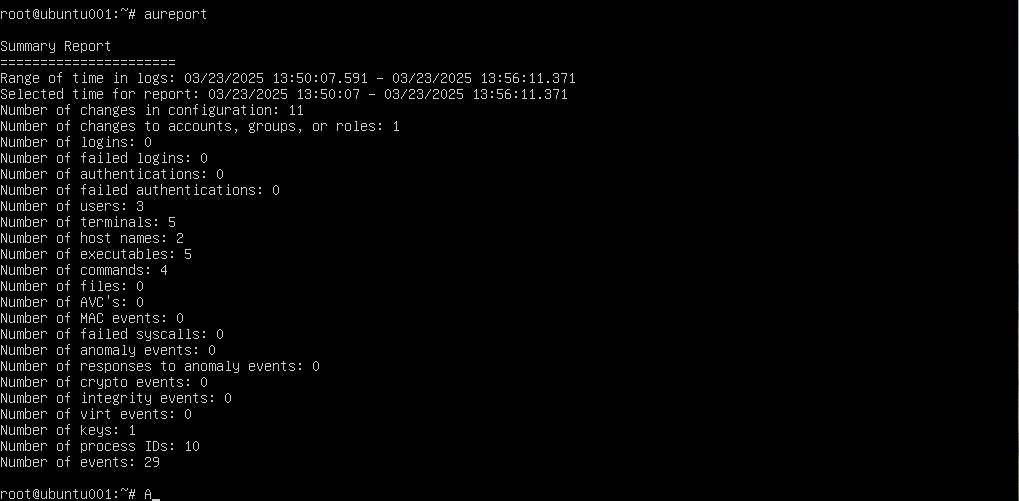
The aureport tool simplifies audit log analysis by generating human-readable reports:
- User Login/Logout Summary:
sudo aureport -l
This report summarizes user login/logout events.
- File Access Summary:
sudo aureport -f
- Failed Login Attempts:
sudo aureport --failed
3. Identify Suspicious Activity
Use ausearch to identify anomalies, such as failed login attempts or unauthorized file modifications:
- Failed Login Attempts:
sudo ausearch -m USER_LOGIN -sv no
- Unauthorized File Access:
sudo ausearch -w /etc/passwd -sv no
4. Centralize Audit Logs
For large-scale environments, centralize logs using tools like rsyslog or integrate with platforms such as:
- ELK Stack (Elasticsearch, Logstash, Kibana): For advanced log analysis and visualization.
- Splunk: For real-time log monitoring and compliance reporting.
- Graylog: For log aggregation and alerting.
Additional Security Measures for Compliance
Beyond configuring audit rules, implementing additional security measures can further enhance compliance:
1. Enable File Integrity Monitoring
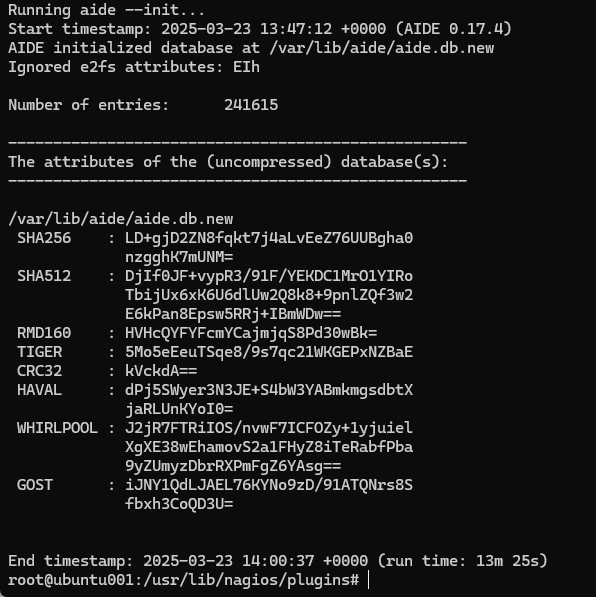
Use tools like AIDE (Advanced Intrusion Detection Environment) to detect unauthorized file changes:
sudo apt install aide
sudo aideinit
Schedule regular integrity checks to detect tampering.
2. Configure Secure Logging
Ensure logs are protected from unauthorized access:
- Restrict access to
/var/log/audit/using permissions:sudo chmod 600 /var/log/audit/audit.log
3. Automate Log Rotation
Prevent audit logs from consuming excessive disk space by configuring log rotation:
sudo nano /etc/logrotate.d/audit
Example configuration:
/var/log/audit/audit.log {
daily
rotate 7
compress
missingok
notifempty
}
4. Monitor System Performance
Audit rules can impact system performance. Use tools like htop or top to monitor resource usage:
sudo apt install htop
htop
Advanced Compliance Tools
1. Automated Vulnerability Scans
# Install OpenSCAP
sudo apt install libopenscap8 ssg-debian
# Run PCI-DSS scan
oscap xccdf eval --profile pci-dss /usr/share/xml/scap/ssg/content/ssg-ubuntu2204-ds.xml
2. Real-Time Alerting with Auditd
# Email alerts for root logins
-a always,exit -F arch=b64 -S execve -F euid=0 -k root_cmd -F exe=/usr/bin/mailx
3. Immutable Audit Logs
#Configure audit.log as append-only
sudo chattr +a /var/log/audit/audit.log
FAQ: Common Compliance Challenges
Q: How long should we retain audit logs for HIPAA?
A: Minimum 6 years. Use logrotate with:
/var/log/audit/*.log {
monthly
rotate 72
compress
}
Q: Can auditd impact server performance?
A: Yes. Monitor with:
watch "grep 'auditd' /proc/slabinfo | awk '{print \$2,\$3}'"
Q: How to prove compliance during audits?
A: Use these commands:
# Generate evidence package
tar czvf compliance-proof-$(date +%F).tar.gz \
/var/log/audit/ /etc/audit/ /var/lib/aide/
Compliance Maintenance Checklist
- Monthly audit rule validation:
auditctl -l | grep -E 'pci|gdpr'
- Quarterly AIDE database updates:
aideinit && mv /var/lib/aide/aide.db.new /var/lib/aide/aide.db
- Biannual firewall rule review:
sudo ufw status numbered
- Annual penetration test:
nikto -h yourdomain.com
Best Practices for Audit and Compliance and Reference Link
To maintain compliance and security, follow these best practices:
- Regular Log Reviews: Schedule routine reviews of audit logs to detect anomalies and ensure compliance.
- Role-Based Access Control: Restrict access to audit logs and sensitive files based on user roles.
- Automated Reporting: Use scripts or tools to automate audit report generation for regulatory requirements.
- Patch Management: Regularly update your server to address vulnerabilities and maintain compliance.
- Test Audit Rules: Periodically test audit rules to ensure they capture required events without causing performance issues.
- Authority Links
Conclusion
Audit and compliance are essential for securing Ubuntu 22.04 servers and meeting regulatory requirements. By leveraging tools like auditctl, ausearch, and aureport, administrators can configure audit rules, monitor system activity, and generate reports to ensure compliance with standards like PCI-DSS, GDPR, and HIPAA. Combining these practices with centralized logging, automation, and additional security measures ensures a robust and compliant server environment.
Stay Tuned for the Next Article!
In the next section of our series, we’ll dive into Web and File Services. Our upcoming article, “Setting Up a Web Server on ubuntu server,” will guide you through installing and configuring Apache or Nginx to host a website. We’ll also cover how to secure your site with SSL/TLS using Let’s Encrypt. Don’t miss it!

9 thoughts on “12. Audit and Compliance for Ubuntu Server: Best Practices”